The identity and access management market is projected to grow from 809 billion in 2016 to 1482 billion by 2021 representing a 129 CAGR. Any use case that doesnt have at least a few alternate flows should be suspect.
Use Cases International Data Spaces
To create a record in a development environment with the same Salesforce ID as in another environment C.

. An Intrusion Detection System IDS is a system that monitors network traffic for suspicious activity and issues alerts when such activity is discovered. Use cases can accurately show the intended design of a system platform or software. Read a QA with authors Reed and Preukschat for.
A use case is a list of steps that illustrate how a process will be carried out in a system. Use plain english and keep it simple. Although nothing indicates that cybercrimes are likely to.
A use-case provides the following benefits. Now that you have a general understanding of what a use case consists of we are ready to start creating our use case. It is a software application that scans a network or a system for the harmful activity or policy breaching.
It uses its extensive attack signature database raises an alarm and sends appropriate notifications on detecting a breach. Despite this significant investment managing digital identities continues to be adversely affected by three Cs cumbersome costly and challenging. They are the antithesis of functional decomposition.
Cybersecurity is in constant hurdles to combat evolving cyber threats. A use case is written. To identify the sObject type in Salesforce D.
Use cases once specified can be denoted both textual and visual representation ie. Use case testing is one of the black box testing techniques used for functional testing of the developed system in order to find any defects. It is an easy means of capturing the functional requirement with a focus on value added to the user.
How to describe Use Cases. What are the benefits of use cases. Benefits of Use Cases.
Use cases specify the expected behavior what and not the exact method of making it happen how. Actor The actor or actors involved. What are two uses for External IDs.
Use-cases force developers to think from the end user perspective. As use cases are written before the development process starts. Providing the best possible outcome scenario.
Authentication for noncredit learners that are registered to our student information system and receive identity records within our central identity store but who may not be generated a UW-Madison credential with which to authenticate to our Learning Management System or other campus systems. 2-The actor is logged in. It ends when the actor closes the Category form.
It outlines from a users point of view a systems behavior as it responds to a request. Actors dont have to be people. A separate set of use cases has been submitted which include no role for central IT or for remembering anything about the person using.
The actor is external to the system. A testing team can take the help of the use. Typically while the name of your use case is being discussed people will start briefly describing the use case.
In the following excerpt of Self-Sovereign Identity Preukschat and co-author Drummond Reed identify how self-sovereign identity use cases make it an attractive option to organizations with benefits that include fraud reduction reduced customer onboarding costs and improved e-commerce sales. Any malicious venture or violation is normally reported either to an administrator or collected centrally using a. Some of the benefits of cybersecurity are.
In this blog well recap the QA session from the day. Use-cases are relatively easy to write and read compared to the traditional requirement methods. A set of use cases has been submitted that describe campus central IT adding social identity people to the central person registry and perhaps associating multiple sets of credentials with an individual.
With data driving the world today digital. To prevent problem behaviors by increasing the perceived risk of discovery and punishment for those who would attack or otherwise abuse the system 2. To describe a use case you need three things.
The use case begins when the actor indicates the intent to view update add or delete Categories record. Head over to our YouTube channel to watch previous sessions in the series subscribe and click on the bell to receive notifications. Each use case includes a high-level summary of the scenario individuals and systems involved in the use case illustrations that show the required steps to achieve the end goal and an icon.
A use case is a written description of how users will perform tasks on your website. To create relationships between records imported from an external system. A UML use case diagram is the primary form of systemsoftware requirements for a new software program underdeveloped.
The use case should have both a main flow sometimes called the basic flow or happy day scenario and alternate flows. It uses test cases that are created based on the use cases to test the system. Use cases describe a large chunk of the system.
The benefits of cyber security include the prevention of data breaches the protection of data the prevention of cyber attacks the detection of cyber threats and the response to cyber incidents. To detect attacks and other security violations that are not prevented by other security measures 3. According to the NISTs documentation on industry best practices there are several compelling reasons to acquire and use an IDS.
There are several benefits to use cases and how they can affect software development and design including. Use Case ID. They can be other systems.
The document walks you through the steps the actor will take to achieve a goal. Choose two A. To prevent an import from creating duplicate records using Upsert.
Each use case is represented as a sequence of simple steps beginning with a users goal and ending when that goal is fulfilled. An actor is a type of user for example bank customer that interacts with the system. 1-The Categories record exists for editingview.
In the fifth webinar from our series on Decentralized Identity Condatis experts Richard Astley and Rob Gathergood presented the benefits and use cases of Self Sovereign Identity. Implementing IDS can prove beneficial for a company as. Name and briefly describe your use case.
UW Madison has several use cases around the use of external identities. These use cases are designed for ICAM Enterprise Architects and business owners and describe some of the most common ICAM business processes. It monitors the working of routers firewall key servers and files.
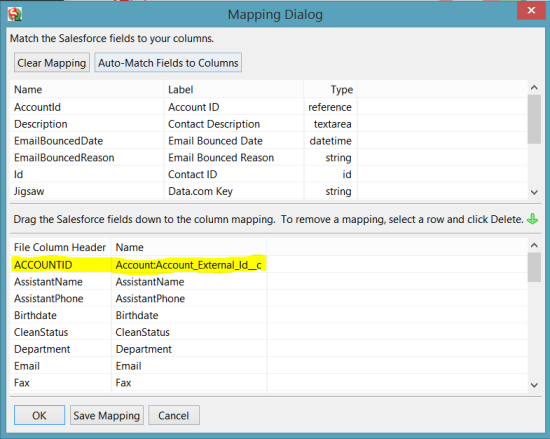
All About Upsert And External Id In Dataloader And Apex Videos Jitendra Zaa S Blog

Using Exernal Id Fields In Salesforce

All About Upsert And External Id In Dataloader And Apex Videos Jitendra Zaa S Blog
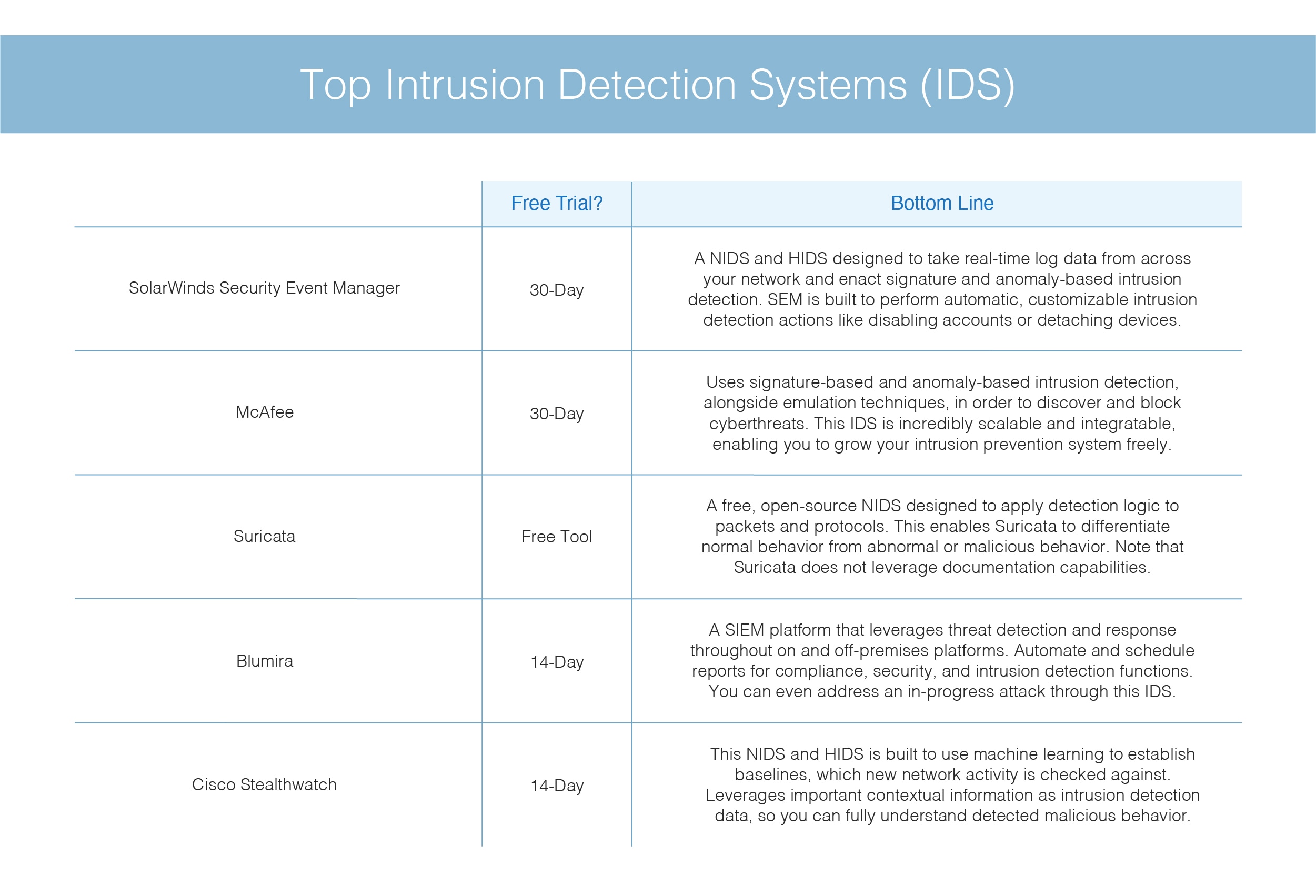
What Is An Intrusion Detection System Ids Definition And Software Solarwinds
0 Comments